BGP does not use a metric to select the best route among alternate routes to the same destination. Instead, BGP uses several BGP path attributes (PA). BGP uses the BGP autonomous system path (AS_PATH) PA as its default metric mechanism when none of the other PAs has been overly set and configured.
After the TCP connection is established, BGP begins with BGP Open messages. After a pair of BGP Open messages has been exchanged, the neighbors have reached the established state, which is the stable state of two working BGP peers. At this point, BGP Update messages can be exchanged.
Peer-group allows fewer configuration commands, and improves processing efficiency by having to prepare only one set of outbound Update packets for the peer group. BGP builds one set of Update messages for the peer group, applying routing policies for the entire group—rather than one router at a time—thereby reducing some BGP processing and memory overhead.
For eBGP connections, Cisco IOS defaults the IP packet’s TTL field to a value of 1, based on the assumption that the interface IP addresses will be used for peering.
Checks Before Becoming BGP Neighbors
1. The router must receive a TCP connection request with a source address that the router finds in a BGP neighbor command.
2. A router’s ASN (on the router bgp asn command) must match the neighboring router’s reference to that ASN with its neighbor remote-as asn command. (This requirement is not true of confederation configurations.)
3. The BGP RIDs of the two routers must not be the same.
4. If configured, MD5 authentication must pass.
BGP uses a keepalive timer to define how often that router sends BGP keepalive messages, and a Hold timer to define how long a router will wait without receiving a keepalive message before resetting a neighbor connection. The Open message includes each router’s stated keepalive timer. If they do not match, each router uses the lower of the values for each of the two timers, respectively. Mismatched settings do not prevent the routers from becoming neighbors.
BGP Messages and Neighbor States
The desired state for BGP neighbors is the established state in which the routers have formed a TCP connection, and they have exchanged Open messages, with the parameter checks having passed. At this point, topology information can be exchanged using Update messages. If the IP addresses mismatch, the neighbors settle into an active state.


Building the BGP Table
The BGP topology table , also called the BGP Routing Information Base (RIB) , holds the network layer reachability information (NLRI) learned by BGP, as well as the associated PAs. Technically, BGP does not advertise routes; rather, it advertises PAs plus a set of NLRI that shares the same PA values. However, most people simply refer to NLRI as BGP prefixes or BGP routes.
The BGP network command instructs that router’s BGP process to do the following:
- Look for a route in the router’s current IP routing table that exactly matches the parameters of the network command; if the IP route exists, put the equivalent NLRI into the local BGP table.
- With this logic, connected routes, static routes, or IGP routes could be taken from the IP routing table and placed into the BGP table for later advertisement. When the router removes that route from its IP routing table, BGP then removes the NLRI from the BGP table, and notifies neighbors that the route has been withdrawn.

Impact of Auto-Summary on Redistributed Routes and the network Command
As it does with IGPs, the BGP auto-summary command causes a classful summary route to be created if any component subnet of that summary exists. However, unlike IGPs, the BGP auto-summary router subcommand causes BGP to summarize only those routes injected because of redistribution on that router. It simply looks for routes injected into the BGP because of the redistribute and network commands on that same router.
The logic differs slightly based on whether the route is injected with the redistribute command or the network command. The logic for the two commands is summarized as follows:
redistribute: If any subnets of a classful network would be redistributed, do not redistribute, but instead redistribute a route for the classful network.
network: If a network command lists a classful network number, with the classful default mask or no mask, and any subnets of the classful network exist, inject a route for the classful network.
For redistribution, the auto-summary command causes the redistribution process to inject only classful networks into the local BGP table, and no subnets. The network command, with auto-summary configured, still injects subnets based on the same logic. In addition to that logic, if a network command matches the classful network number, BGP injects the classful network, as long as at least any one subnet of that classful network exists in the IP routing table.
Manual Summaries and the AS_PATH Path Attribute
BGP manual summarization with the aggregate-address command can summarize based on any routes in the BGP table, creating a summary of any prefix length. It does not always suppress the advertisement of the component subnets, although it can be configured to do so. The aggregate route must include the AS_PATH PA, just like it is required for every other NLRI in the BGP table.
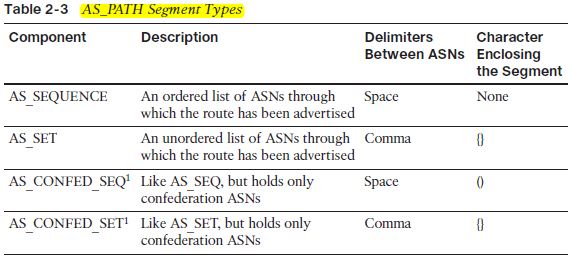
The AS_PATH PA consists of up to four different components, called segments , as follows:
- AS_SEQ (short for AS Sequence)
- AS_SET
- AS_CONFED_SEQ (short for AS Confederation Sequence)
- AS_CONFED_SET
When the component subnets of the summary route have differing AS_SEQ values, the router simply can’t create an accurate representation of AS_SEQ, so it uses a null AS_SEQ. However, this action introduces the possibility of creating routing loops.
The AS_PATH AS_SET segment solves the problem when the summary route has a null AS_SEQ. The AS_SET segment holds an unordered list of all the ASNs in all the component subnets’ AS_SEQ segments.
"atomic-aggregate" refers to the fact that the ATOMIC_AGGREGATE PA has also been set; this PA simply states that this NLRI is a summary.

The following list summarizes the actions taken by the aggregate-address command when it creates a summary route:
- It does not create the summary if the BGP table does not currently have any routes for NLRI inside the summary.
- If all the component subnets are withdrawn from the aggregating router’s BGP table, it also then withdraws the aggregate. (In other words, the router tells its neighbors that the aggregate route is no longer valid.)
- It sets the NEXT_HOP address of the summary, as listed in the local BGP table, as 0.0.0.0.
- It sets the NEXT_HOP address of the summary route, as advertised to neighbors, to the router’s update source IP address for each neighbor, respectively.
- If the AS_SEQ of the component subnets differs in any way, it sets the AS_SEQ of the new summary route to null.
- When the as-set option has been configured, the router creates an AS_SET segment for the aggregate route, but only if the summary route’s AS_SEQ is null.
- It suppresses the advertisement of all component subnets if the summary-only keyword is used, advertises all of them if the summary-only keyword is omitted, or advertises a subset if the suppress-map option is configured.

Adding Default Routes to BGP
Default routes can be injected into BGP in one of three ways:
- By injecting the default using the network command
- By injecting the default using the redistribute command
- By injecting a default route into BGP using the neighbor neighbor-id defaultoriginate [ route-map route-map-name ] BGP subcommand
When you inject a default route into BGP using the network command, a route to 0.0.0.0/0 must exist in the local routing table, and the network 0.0.0.0 command is required.
Injecting a default route through redistribution requires an additional configuration command—default-information originate . The default route must first exist in the IP routing table.
Injecting a default route into BGP by using the neighbor neighbor-id default-originate [ route-map route-map-name ] BGP subcommand does not add a default route to the local BGP table; instead, it causes the advertisement of a default to the specified neighbor. In fact, this method does not even check for the existence of a default route in the IP routing table by default, but it can.
ORIGIN Path Attribute
The ORIGIN PA provides a general descriptor as to how a particular NLRI was first injected into a router’s BGP table. Routes redistributed into BGP from an IGP actually have an ORIGIN code of incomplete.
BGP Update Message
If a router needs to advertise a set of NLRIs, and each NLRI has a different setting for at least one PA, separate Update messages will be required for each
NLRI. However, when many routes share the same PAs—typical of prefixes owned by a particular ISP, for example—multiple NLRIs are included in a single Update. This reduces router CPU load and uses less link bandwidth.
For a route to be a candidate to be considered best, the NEXT_HOP must be either
- 0.0.0.0, as the result of the route being injected on the local router.
- Reachable according to that router’s current IP routing table. In other words, the NEXT_HOP IP address must match a route in the routing table.
Note that the NEXT_HOP PA cannot be set through a route map.
For the received-routes option to work, the router on which the command is used must have the neighbor neighbor-id soft-reconfiguration inbound BGP subcommand configured for the other neighbor.
These show ip bgp neighbor commands with the advertised-routes option list the BGP table entries that will be advertised to that neighbor. However, note that any changes to the PAs inside each entry are not shown in the command output.
Summary of Rules for Routes Advertised in BGP Updates
The following list summarizes the rules dictating which routes a BGP router sends in its update messages:
- Send only the best route listed in the BGP table.
- To iBGP neighbors, do not advertise paths learned from other iBGP neighbors.
- Do not advertise suppressed or dampened routes.
- Do not advertise routes filtered through configuration.
Adding eBGP Routes to the IP Routing Table
Cisco IOS Software uses simple logic when determining which eBGP routes to add to the IP routing table.
- The eBGP route in the BGP table is considered to be a “best” route.
- If the same prefix has been learned through another IGP or through static routes, the AD for BGP external routes must be lower than the ADs for other routing source(s).
BGP sets the AD differently for eBGP routes, iBGP routes, and for local (locally injected) routes—with defaults of 20, 200, and 200, respectively.
The actual IP route added to the IP routing table contains the exact same prefix, prefix length, and next-hop IP address as listed in the BGP table—even if the NEXT_HOP PA is an IP address that is not in a connected network. As a result, the IP forwarding process might require a recursive route lookup.
Backdoor Routes(network backdoor) will use the local AD (default 200) for the eBGP-learned route to network.
Adding iBGP Routes to the IP Routing Table
Cisco IOS has the same two requirements for adding iBGP routes to the IP routing table as it does for eBGP routes:
- The route must be the best BGP route.
- The route must be the best route (according to the AD) in comparison with other routing sources.
Additionally, for iBGP-learned routes, IOS considers the concept of BGP synchronization.
The key to understanding BGP sync is to know that redistribution solves the routing
black-hole problem, and sync solves the problem of advertising a black-hole route to
another AS.
The BGP sync logic controls that decision as follows: Do not consider an iBGP route in the BGP table as “best” unless the exact prefix was learned through an IGP and is currently in the routing table. The route must be IGP-learned not via own's static route.
Sync includes an additional odd requirement when OSPF is used as the IGP. If the OSPF RID of the router advertising the prefix is a different number than the BGP router advertising that same prefix, sync still does not allow BGP to consider the route to be the best route.
Disabling Sync and Using BGP on All Routers in an AS
A second method to overcome the black-hole issue is to simply use BGP to advertise all the BGP-learned prefixes to all routers in the AS. BGP needs the full mesh of iBGP peers inside an AS because BGP does not advertise iBGP routes (routes learned from one iBGP peer) to another iBGP peer. BGP offers two tools (confederations and route reflectors) that reduce the number of peer connections inside an AS, prevent loops, and allow all routers to learn about all prefixes.
Confederations
Peers inside the same sub-AS are considered to be confederation iBGP peers , and routers in different subautonomous systems are considered to be confederation eBGP peers. Confederation eBGP peer connections act like true eBGP peers in some respects. In a single sub-AS, the confederation iBGP peers must be fully meshed, because they act exactly like normal iBGP peers.
Confederations prevent loops inside a confederation AS by using the AS_PATH PA. BGP routers in a confederation add the subautonomous systems into the AS_PATH as part of an AS_PATH segment called the AS_CONFED _SEQ. (The AS_PATH consists of up to four different components, called segments—AS_SEQ, AS_SET, AS_CONFED_ SEQ, and AS_CONFED_SET.

The following list summarizes the key topics regarding confederations:
- Inside a sub-AS, full mesh is required, because full iBGP rules are in effect.
- The confederation eBGP connections act like normal eBGP connections in that iBGProutes are advertised—as long as the AS_PATH implies that such an advertisement would not cause a loop.
- Confederation eBGP connections also act like normal eBGP connections regarding Time to Live (TTL), because all packets use a TTL of 1 by default. (TTL can be changed with the neighbor ebgp-multihop command.)
- Confederation eBGP connections act like iBGP connections in every other regard—for example, the NEXT_HOP is not changed by default.
- Confederation ASNs are not considered part of the length of the AS_PATH when a router chooses the best routes based on the shortest AS_PATH.
- Confederation routers remove the confederation ASNs from the AS_PATH in Updates sent outside the confederation; therefore, other routers do not know that a confederation was used
Route Reflectors
In an iBGP design using RRs, a partial mesh of iBGP peers is defined. Some routers are configured as RR servers; these servers are allowed to learn iBGP routes from their clients and then advertise them to other iBGP peers. Note that only the RR server itself uses different logic, with clients and nonclients acting as normal iBGP peers.
One of the main motivations for using RRs is to allow sync to be disabled.
RR feature uses several tools to prevent loops, as follows:
CLUSTER_LIST: RRs add their cluster ID into a BGP PA called the CLUSTER_LIST before sending an Update. When receiving a BGP Update, RRs discard received
prefixes for which their cluster ID already appears. As with AS_PATH for confederations, this prevents RRs from looping advertisements between clusters.
ORIGINATOR_ID: This PA lists the RID of the first iBGP peer to advertise the route into the AS. If a router sees its own BGP ID as the ORIGINATOR_ID in a received route, it does not use or propagate the route.
Only advertise the best routes: RRs reflect routes only if the RR considers the route to be a “best” route in its own BGP table. This further limits the routes reflected by the RR. (It also has a positive effect compared with confederations in that an average router sees fewer, typically useless, redundant routes.)
Multiprotocol BGP
Some of these configurations carry VPN-IPv4 routes, some only IPv4 routes, and others carry VPN-IPv4 and IPv4 routes. The type of BGP session and the specification of which routes the peering sessions will carry are controlled through the use of the address families.
Configure a BGP address family for each Virtual Routing and Forwarding (VRF) configured on the PE router and a separate address family to carry no IPv4 routes between PE routers. The initial BGP process, the portion of the configuration that cites no address family specifications, becomes the default address family. This default context becomes the “catch all” where any non-VRF-based or IPv4-specific sessions can be configured. Any prefixes learned or advertised in this default address family will be injected into the global routing table. The configuration of these BGP sessions is exactly the same as the standard BGP configuration with the exception that the session needs to be activated.
R1(config-router)# address-family vpnv4
R1(config-router)# neighbor 194.22.15.3 activate
The configuration of the VPNv4 address family also adds a further command to the BGP configuration to support the MP-BGP-specific extended community attributes. This command will be added by the IOS by default and is necessary because it instructs BGP to advertise the extended community attributes.
The default behavior is to send only the extended community attribute. If the network design requires the standard community attribute to be attached to these non-IPv4 prefixes, this behavior can be changed through the neighbor 194.22.15.3 send-community both command.
Note that MP-iBGP communicates these routes across the MP-iBGP sessions running between PE routers. To this end, the routing context must be configured under the BGP process to communicate to BGP which VRF prefixes it needs to advertise.
Summary
address-family vpnv4
- BGP mode; allows the creation of the MP-BGP session necessary to form the VPNv4 session between PE devices
bgp client-to-client reflection
- BGP mode; on by default, tells an RR server to reflect routes learned from a client to other clients
default-information originate
- BGP mode; required to allow a static default route to be redistributed into BGP
distance bgp external-distance internal distance local-distance
- BGP mode; defines the administrative distance for eBGP, iBGP, and locally injected BGP routes
neighbor { ip-address | peer-group-name } default-originate [ route-map map-name ]
- BGP mode; tells the router to add a default route to the BGP Update sent to this neighbor, under the conditions set in the optional route map
show ip bgp injected-paths
- Exec mode; lists routes locally injected into BGP